Due to the Governor specifically naming Private Investigators as non essential and prohibited from operation in March we are not operating now.
I do not believe any of what the Governor and his “health department” are telling us.
Due to the Governor specifically naming Private Investigators as non essential and prohibited from operation in March we are not operating now.
I do not believe any of what the Governor and his “health department” are telling us.
With the recent rash of vehicle break ins, where the garage door opener and registrations were taken – first thing you need to do is make that old opener not work. First – unplug the opener. That is quick and dirty but will stop them until you take a more permanent step. you need to make that old opener useless permanently.
Some older models there is a set of switches on the opener that set the code. The remotes have the same inside. Just flip a few of the switches on the opener to the other position and then make the switches in any remaining or new remotes match – job done.
Most newer openers learn the remote and will have a button to make it forget the remotes (all of them). Then you need to have it re learn the existing remotes or the button built into newer vehicles. Then the missing remote will be useless ( unless it is recovered and then you can have the opener re learn it).
There may be a different process for the openers that are IOT (Internet of Things) connected through wifi.
DO NOT, as someone posted in a comment elsewhere, booby trap your car to injure the thieves – in today’s lawsuit happy world – not a good idea! Besides it would probably damage your car and the insurance might well decline to pay.
Another method that can breach the security of your garage and probably thereby your home is to toggle from out side, the release mechanism needed to open the garage door in a power failure. This little handle on a rope hanging down from the point where the mechanism moves on the track just needs a pull to make your garage door unlocked and able to open manually. The miscreant can work a hook between the top of the door and the opening, grab the rope and give it a pull and the door will open.
A quick fix would be to remove the little red handle and make sure the rope isn’t long enough to reach outside the top of the door. That could also make it difficult to open in an emergency. Better might be to use a light string – kite string – to tie the rope to the arm that attaches to the door in a way that it can’t be easily snagged from outside.

Sometimes interesting things happen in investigations. Here are a few recent examples:
Needed to find out if a guy was living with another woman not far from me, decided to do reconnaissance. Prepared a ruse for coming to the door and asking for him. This is something I often do,, I put some paper in an envelope and wrote the guy’s first and last name on it. I had a picture of the guy – he was black about 50. Drove up the cul de sac expecting to just drive by verify which house and then come back on foot to knock the door. Well, there he was out front watering the lawn. I really just needed usable picture of him but video would be better – Started my phone video, slipped it in my shirt pocket with the lens poking out. Walked over to him and asked if, what ever the name was – lived there. He said “that’s me, I live here.”
I gave a surprised look, said ” I think I found the wrong guy, I’m supposed to serve these court papers but I know it is the wrong guy, he’s 22 and white.” Job done.
A client had been victimized – the culprit had been identified and a warrant was issued but until the culprit was arrested no court resolution or restitution would be possible. I found several possible addresses and cars that the culprit was associated with, found their social media posts with Denver Broncos fan posts. I took advantage of that – made a visit to the several addresses until I found the culprit’s car parked at one, called the local police and waited until officer’s arrived and arrested the culprit – in Bronco orange jersey in the middle of the game.
Looking for a suspected sexual predator who was believed to be living with or near relatives I tracked the parents and a brother to two houses about two blocks apart. I found that cars parked at those addresses were registered to the parents but under aliases and variations of their names – using the common Hispanic name traditions of sometimes using father’s surname, mother’s surname, husband’s surname, the wife using de husband’s surname,. One car had “changed hands” from the wife using her husband’s last name to the wife using her mothers surname. I also found evidence of the culprit using a car registered to someone who he is friends with on social media. I found a company he and family members own with a fake address in the middle of a city golf course. I was able to finally locate the culprit using social media information about when they would be at a particular location.
In a contested divorce case I determined that the husband had a new live in girl friend. While I was investigating him and his assets, he appears to have had the girlfriend buy a birthday present for his 6 year old daughter who lives in another state with the wife. She ordered online three Hello Kitty wines! Cannot imagine what she was thinking, was it spite against the wife or against her boyfriend? Had no idea there were Hello Kitty wines!
 A husband needed to find his estranged wife to serve her with divorce papers, he had two possible areas of the city where she might be. As a precaution I checked for restraining orders and found that not only did his wife have one against him, he had one against her so I couldn’t let either of them know the others whereabouts. He did have a lawyer so I told him I could work through the lawyer only. I tracked down a likely address for her and went there knocked on the door and a young woman answered. I had a picture of the wife and this was not her. I asked if the wife was there she said she doesn’t live there anymore. I asked is she had any forwarding address. A teen aged kid behind her pops up and says she is in rehab in California. The woman agreed with that, but did admit she had a phone number that might or might not be still working. I thanked her and went back to the car and called the number, asked for the wife, and it was she who answered. I explained to her that her husband hired me to find her so she could be served and get the divorce going after these two years. She agreed that would be good, to get it done but was very leery about telling me where she lived or worked but she told me what part of town and said the next evening after she got off work would be good. I said no problem maybe someplace like Starbucks? She eventually agreed to meet at a police station which was okay by me. The next day she let me know which police station it was twenty miles from where she had claimed to be. The next day I talked to the husband, he admitted he had been living in his truck in a mountain campground. I never did know where either was really living but he paid cash and the papers were served.
A husband needed to find his estranged wife to serve her with divorce papers, he had two possible areas of the city where she might be. As a precaution I checked for restraining orders and found that not only did his wife have one against him, he had one against her so I couldn’t let either of them know the others whereabouts. He did have a lawyer so I told him I could work through the lawyer only. I tracked down a likely address for her and went there knocked on the door and a young woman answered. I had a picture of the wife and this was not her. I asked if the wife was there she said she doesn’t live there anymore. I asked is she had any forwarding address. A teen aged kid behind her pops up and says she is in rehab in California. The woman agreed with that, but did admit she had a phone number that might or might not be still working. I thanked her and went back to the car and called the number, asked for the wife, and it was she who answered. I explained to her that her husband hired me to find her so she could be served and get the divorce going after these two years. She agreed that would be good, to get it done but was very leery about telling me where she lived or worked but she told me what part of town and said the next evening after she got off work would be good. I said no problem maybe someplace like Starbucks? She eventually agreed to meet at a police station which was okay by me. The next day she let me know which police station it was twenty miles from where she had claimed to be. The next day I talked to the husband, he admitted he had been living in his truck in a mountain campground. I never did know where either was really living but he paid cash and the papers were served.
Workers Comp case, a guy out of work seemed to be working, needed to be caught. Knowing he had no license after a DUI it seemed likely he was taking a bus or light rail. On Sunday, not expecting him to be working, I parked near his apartment on the likely route in order to scope out the possibilities, with video cameras aimed at the bus/train station and his apartment I was watching the buses, trains and people. Out of no where he shows up behind my vehicle walking across to a convenience store. Reviewing the videos later I did not see him walking from the apartment or from the bus / train. There is a chain link fence that whole block with no gates or gaps where had he come from? By syncing the videos I saw a white cargo van come from the direction of the apartment but did not appear in the other view for almost a minute. He had been in the van and they dropped him off right across the street from me. Well I now knew what to look for as his transport to and from work.
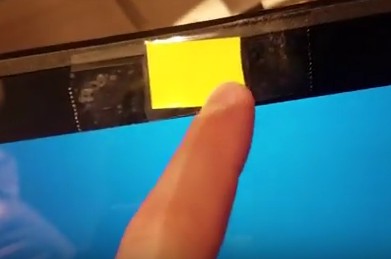
Last night my middle school grand daughter got out her Chromebook to do some homework. Her dad, seeing a stirp of yellow paper at the top of the screen asked ” Is that a sticky note over your camera?”
“Yeah, a Sheriff told me I should.”
Good advise. Especially on a device that relies on being on-line with the Internet, being aware that bad people can hack into the systems and do things like turning on your camera, and take pictures of you, is wise.
There is an Internet scam going around that deals with this. The email comes in and the subject is something like “xyz123! is your password”.
Well, if you have ever used that as your password it will pique your interest! Then it says the sender has hacked your computer with malware, has got your personal information and wants you to send a payment in bitcoin to him and provides a link. Then, he says, if you don’t he will send the embarrassing or obscene or whatever videos he claims to have captured from your camera to all your contacts from your email or Facebook or whatever.
Wow, the guy must have actually hacked your computer – you got to send him the bitcoins – right? Well, absolutely not!
Lets go back – the thing that got your attention – the password! Okay, it is a password you have used – probably one that you used to log in to sites that didn’t really mean anything, maybe to get free access to something, a newsletter, a free game, almost anything. It could be a password you used on several sites like that figuring you would just get junk emails.
So that site could be a false front put up simply to gather email addresses (which are saleable in quantities) and —- PASSWORDS. So this “hacker” probably bought a list of email addresses and passwords (and whatever other information you gave to log in to the site) and he is in business.
If you do anything except delete the email and ignore it, he will probably get more info from you in his fishing expedition. And certainly if you send bitcoins to the link he provides that will be in his pocket (or more likely in some Russian, Chinese or Nigerian organization’s bank account).
Even if he did have all your contacts and compromising pictures what makes you think sending $600 worth of bitcoins (for some reason $600 seems to be the number they start with) will be the end of it? But, they won’t send anything to anyone – if they did it would make it a bigger crime and would make it much more likely that the FBI or someone would become involved and they could get caught.
If you get one of these emails, you probably will get more similar ones, from different email addresses. The list gets sold to more than one creep, they all figure that for a little work sending these emails hoping for a bite, they will get the payoff.
What should you do? Well first off, stop using throwaway passwords particularly on sites that you would not want to be hacked. Change your passwords regularly and make them something like “hjU^764Kkidrq!O0zl”.
You might create a throw away email on hotmail or yahoo or something using a fake name and fake info and use that when you sign into sites that don’t mean anything (or just don’t sign into those kinds of sites). And never, ever use the same user name and password on more than one site.
Wow,

While the tile key locator is not actually a GPS device because it is constantly looking for a nearby bluetooth device with the tile ap and that device will by default have GPS it is able to find something lost away from your phone or home.
When you install the tile ap on your device – usually your phone – it sets up a link into the cloud based service provided by Tile.
When the Tile is lost, and any device with the Tile ap comes within bluetooth range that device in the background, forwards to the cloud the current GPS coordinates of that device and therefore the Tile.
When you want to find the Tile you click the find on the ap, your device sends the request to the cloud, the cloud responds with the current location and your ap displays the Tiles last know location.
The tile is sold as a key finder but it will work on about anything, a purse, a dog, a car, just about anything. With a little imagination it could find a lost child, or missing spouse, it is your imagination. Now if you were to use it to find your wayward spouse you probably should not activate the find my phone feature to your own phone – it will ring your phone if the button on the Tile is pressed twice.
The recent rash of smash and grab burglaries in Parker and other Metro Denver areas look to me to be targeting mostly small store front businesses. They break out whatever windows face the street, enter and try to grab the cash drawers.
My guess is they pick their targets based on them being small retail or food businesses. They of course are avoiding bigger businesses that probably have more security, particularly burglar alarms. None of the news accounts have mentioned alarms. Several did have video systems but hoodies and ski masks protect them from these. They have stayed away from places that are well lit at night – and where there are all night businesses with traffic in the parking lots. They are obviously not looking for large pots of cash, most of their targets would have no more cash on hand than is required for making change to the customers coming in the morning. They did not seem to be interested in any merchandise that would been easier to track when the had to convert it to cash.
They seem to be young opportunists, using rocks and their feet to break in. This means that if stopped on their way to the break in, they have no weapons or tools on them.
They obviously have a car but don’t seem to have parked too close to the target business. Some of the cash drawers were found dumped in a local church parking lot. An unlighted parking lot with no close by homes. Also significant, that church is off Parker road and an unlikely spot for most people to even know about – unless that were traveling that road to get out of the area without being on the well lit and more heavily traveled Parker Rd. What is up that road – a back route into Aurora, with no traffic and very few lights and a quick exit from Parker and Douglas County – the jurisdictions where the break ins happened. Less likely the Aurora PD or Arapahoe County Sheriff would be alerted.
I haven’t looked at the break ins reported in Arvada and Lone tree but if they are related, it seems the locations are also located near city and county boundaries where a jurisdictional jump is easier. There don’t seem to have been any reported in Aurora or Denver – both with large police departments.
What could be done to prevent these? Better lighting might help. Not much else – they did not seem to be doing much if any planning, so signs saying no cash left over night probably would not help. Maybe eliminate any rocks or other objects near the doors and windows. Alarm systems, with loud interior and exterior bells or sirens might scare them off but probably not before much of the damage happened. Even an empty cash drawer outside of the cash register did not deter them. Not leaving cash where smash and grab punks can get it will help deter future punks. If there is no pay off the word will get around.
It was surprising that they hit the same area of Parker two days in a row. That was careless and speaks to their laziness and low intelligence. They seem to have some street “smarts” – not carrying break in tools and dumping the cash drawers quickly. The hoodies and masks as well. But they are stupid in targeting businesses where the likely cash take will be $100 or so. I would not be surprised if these idiots were from Aurora, maybe Denver. Street punks. They will either get caught or graduate to something more dangerous or with higher “profit”.
 The Supreme Court (US) has several times issued “guidance” on what can and cannot be considered private property in searches under the Fourth Amendment.
The Supreme Court (US) has several times issued “guidance” on what can and cannot be considered private property in searches under the Fourth Amendment.
The current status is – and always subject to further review by the court in future cases – the inside of your home and it’s “curtilage” require a search warrant (in most cases) for police to perform a search. But what is curtilage? Well it is such a little used word that most dictionaries will claim it to be misspelled. It is that part of your home that is a part of it, not the house itself. It may be your fenced yard, unless maybe it is so large as to be considered an open field. It might be your driveway, if it is not a likely pathway where friends, neighbors, solicitors, the mailman or politicians might approach your door to knock. It might be an area behind a section of fence or screening that blocks it from the street. But, it is not your front porch, unless you have a security fence that would prevent unwanted neighbors or politicians or whatever from reaching it.
Here is a link to the article quoted above: https://verdict.justia.com/2018/07/18/collins-v-virginia-an-innocuous-fourth-amendment-decision-about-curtilage
Do you suspect your spouse is having an affair? Statistics show that most people who suspect it or just have a gut feeling are right. Maybe you need to  know for sure so you can force them to get couples counseling to try to save the marriage or so you can just get past it or to make a decision on whether to move forward to a divorce.
know for sure so you can force them to get couples counseling to try to save the marriage or so you can just get past it or to make a decision on whether to move forward to a divorce.
Although divorce in Colorado is No Fault and evidence of cheating is not required, that evidence can sometimes be leveraged to affect the value of a property settlement or just to convince the spouse to not fight. That evidence can be important to your future economic situation.
It can also affect child custody in some cases.

I realize that since my work involves sometimes trying to find information that people try to hide this could be counter productive, frankly, there are good reasons to protect your data from other people. Things like financial records, private pictures, ideas for a business you plan to start, company trade secrets, lots of things that just should not be out in plain sight.
Storing things on your computer or phone or other device can leave it available to hackers or even just someone who randomly gets physical access to the device. Anti virus software, pass codes on the device, other things mean little if the info is stored as a simple file, like a word document or photo or video.
And sending a file by email or on a thumb drive or DVD is also risky. Unless the file is encrypted.
Enter some free software that can encrypt your file, called GPG – it comes as part of Linux operating systems and is available for Windows as GPG4win. It relates back to what was originally called PGP which was Pretty Good Privacy. It uses a two key system – a public key and a private key. There are phone aps that use PGP – these are not free but worth looking at.
You can use it to make an encrypted copy of a file that without your key (a long series of random characters – letters, numbers and symbols) the file is useless.
If you need someone to send you something – emailed or otherwise – they will need the free program on their end and your public key. The public key encrypts only – it will not change the encrypted file back, so it doesn’t matter who happens to get the file or the key, only your private key can unlock it.
Now that’s not to say that the NSA or someone with unlimited time on massive computers could not get the key, but as long as you are not a criminal or terrorist it is very doubtful anyone would be able to get your data.
As to storing the keys for your encrypted files, try one of these password managers in this article .
There are lots of scams going around. Some are obvious (to most people) like the ones that misspell obvious words. Or mention that it is a Nigerian Prince that died and left a boatload of money you can get.
One that tried to get passed me recently was one claiming to be PayPal.com telling me there was a problem with my account and it had an email that had something like PayPal.audit.com and it had a link to click that also had PayPal in the address. I’ve seen and heard similar scams from “Visa” or “Mastercard” or “Discover” – really any place that handles money. All of these scams rely on people just carelessly clicking the link or returning the email. If you should click the link you will probably see a web page that resembles or even exactly matches a real web site for the company – it will ask you to log in. Guess what will happen to your log in info? For sale instantly on the Dark Web. Bad guys will have access to everything on that account. They can go in and drain the account, run up the debt, change the password, change the email or phone number. Nothing good will happen!
The best way to handle anything like this is probably to just delete it. Certainly do not respond in any way. Then you could go to the real site – by typing the PayPal.com or Visa.com or whatever and logging in to the real site and while you are there maybe look at the charges or whatever, see if there is a notice to users about the scam you encountered, perhaps send a message to the site support people that there is a scam – they might ask you to send a copy of the message – if you haven’t deleted it.
You might even without having a scam arrive go to all your accounts and change the password – and make them difficult to guess like H2#wQ7^J^&%hakeut#(!
Get and use on of the available wallet apps that will store all your passwords and log ins for you so those impossible to remember passwords and keep them secure and encrypted. Check out Norton security or McAfee or some other apps that protect from viruses and malware and intrusions and include a wallet function.
The Norton Security also can include LifeLock protection, the password wallet,

Apple’s Wallet (used to be Passport) also lets you use your iPhone to replace your credit cards at the point of sale.
